
Developers are increasingly voicing their opinions through their open source projects in active use by thousands of software applications and organizations.
To do this, a maintainer adds broken code, protest messages, or undesired damaging functionality in the latest versions of their project without documenting it beforehand.
When an existing application fetches the latest version of the project, the newly added code gets pulled in and runs by surprise.
Most recently, the developer of the 'event-source-polyfill' npm package has peacefully protested Russia's "unreasonable invasion" of Ukraine, to Russian consumers.
While for the longest time open source software has been reliable, community-fuelled, and efficient in that it takes out the need to reinvent the wheel, the recurring cases of voluntary self-sabotage by maintainers have cast doubts on the overall reliability of the ecosystem.
Third 'protestware' of 2022
On March 17th, Russia-based developer Viktor Mukhachev aka Yaffle added an interesting piece of code to his popular npm library 'event-source-polyfill'.
Polyfill packages are designed to implement existing JavaScript features on web browsers that may not support them. As such, the package in question expands Mozilla's 'EventSource' APIs to other browsers that may lack the concept.
And this would explain why the package is used by well over 135,000 GitHub repositories and downloaded over 600,000 times weekly on npm.
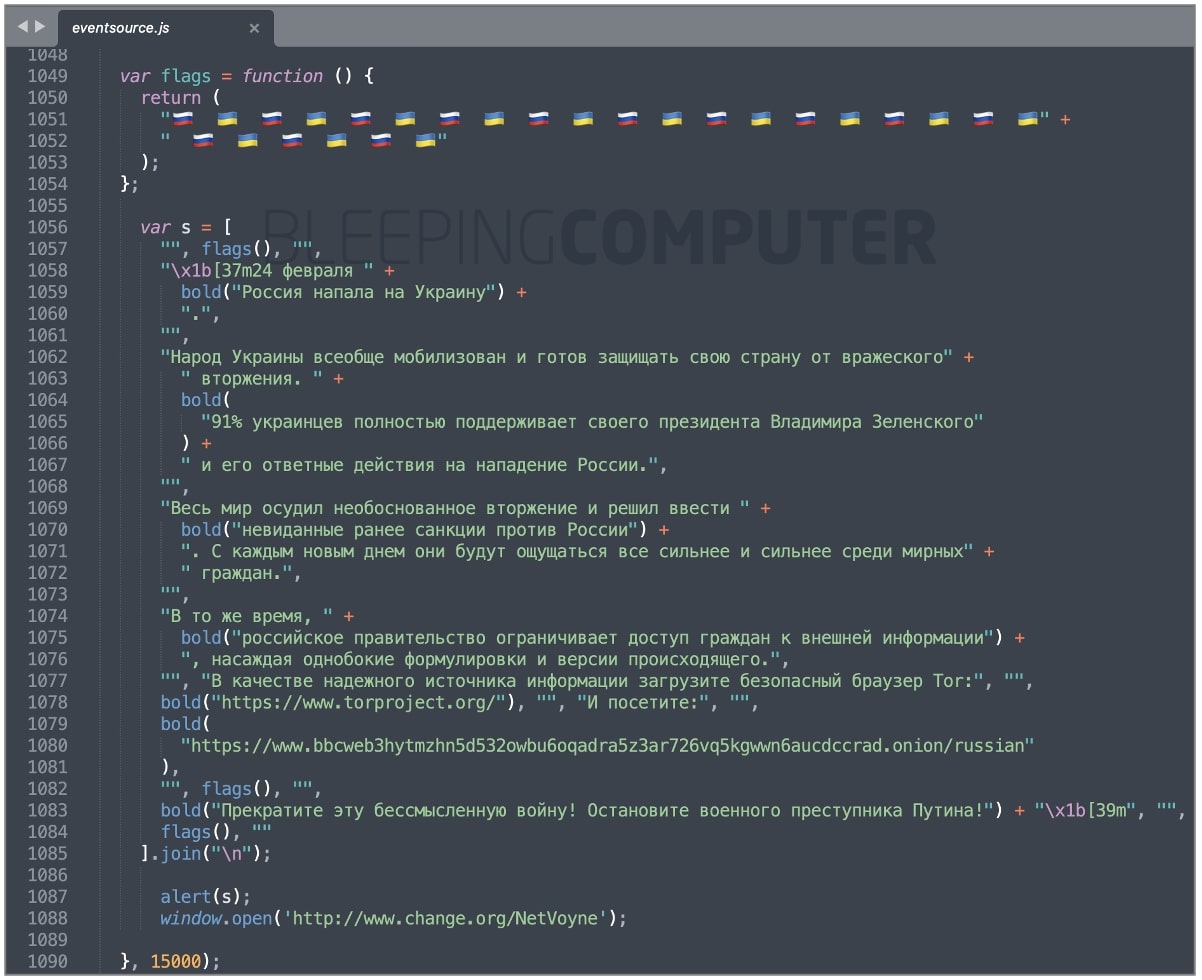
However, a change introduced in version 1.0.26 of 'event-source-polyfill', as seen by BleepingComputer, means applications built with the library will show anti-war messages to Russia-based users after 15 seconds of launch.
As of today, the new version continues to be up on npm and GitHub, nearly four weeks after it went live.
This marks the third major protest of 2022 by an open source developer leveraging his vastly used software to express opinions on a matter of public interest.
In fact around the same time as 'event-source-polyfill' turned into protestware, several other vastly popular packages followed suit.
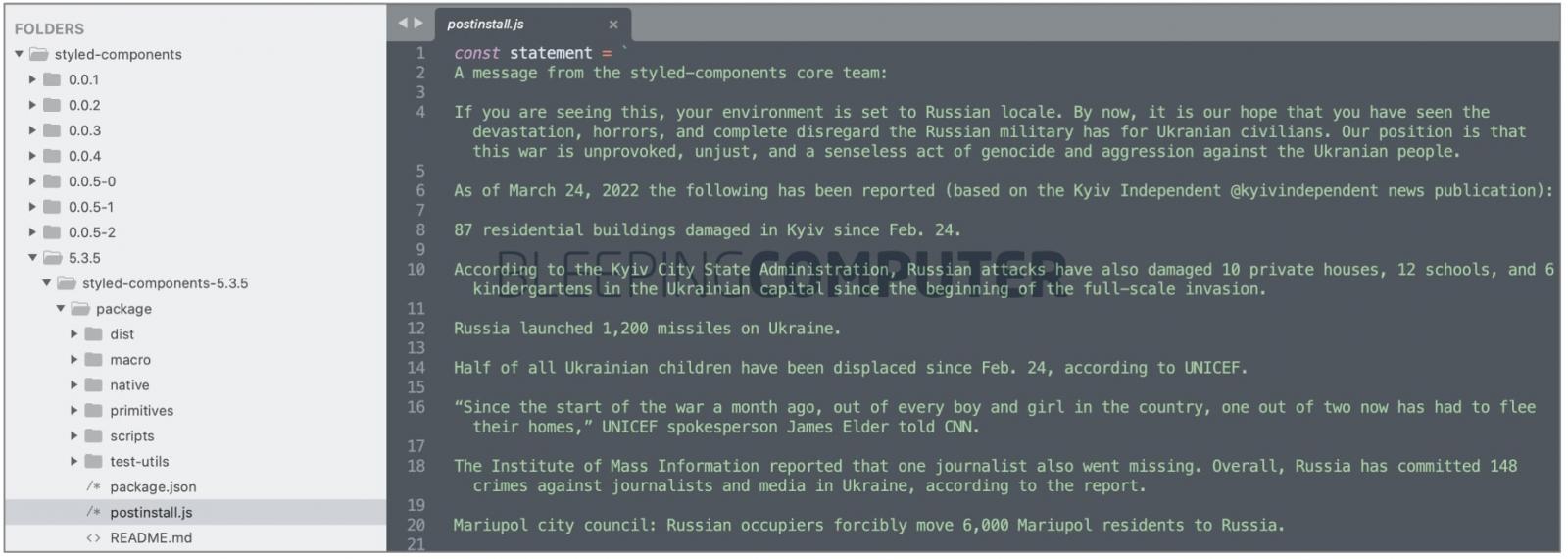
The 'es5-ext' and 'styled-components' are just some examples of real npm packages with millions of weekly downloads turned protestware, as analyzed by software security company Checkmarx.
In 2016, the 28-year-old Azer Koçulu broke the internet by withdrawing his popular 'left-pad' library from the npm registry. The far-reaching impact compelled former npm CTO Laurie Voss to restore the removed versions of left-pad.
January's sabotage of 'colors' and 'faker' libraries in protest by their maintainer potentially broke thousands of production applications that were using the dependencies.
Whereas, the outright destructive version of 'node-ipc' released last month by its developer deleted all data on the hard drive of users it believed were Russian or Belarusian.
The case of 'event-source-polyfill', however, is more benevolent —akin to a peaceful protest.
Rather than deleting any data or breaking applications, the application urges Russia to end its "unreasonable invasion" of Ukraine and prompts Russian civilians to seek reliable news sources.
"The people of Ukraine are universally mobilized and ready to defend their country from the enemy... 91% of Ukrainians fully support their President Volodymyr Zelensky and his response to the Russian attack," writes Yaffle within the library.
"The whole world condemned the unreasonable invasion and decided to enter unprecedented sanctions against Russia. With each new day, they will be felt more and more strongly among the civilians."
Citing concerns over Russia's control over information that gets disseminated to the civilians, the developer urged users to beware of "one-sided" news and go to reliable sources, giving BBC's Tor website as an example.
Lastly, after appealing to Russian President Putin to end this "senseless" war, the newly added code directs the user to a Change.org petition that's been signed by over 1.2 million people to date.
Self-sabotage breeds trust issues
Heroic as these self-sabotage incidents might be for many, for some they cross an ethical line and have posed a new challenge that everyone must now worry about: the trustworthiness and reliability of open source libraries.
In particular, the 'colors' sabotage led to mixed reactions—some praising the maintainer for taking a stance against big corporations who use open source without funding it.
In contrast, the publication of destructive 'node-ipc' versions drew sharp criticism from developers, with some calling it "a huge damage" to the credibility of the whole open source community.
But, 'event-source-polyfill' may not fall in the same league:
"The popup message is information that there's a war going on, and a suggestion to download the Tor browser (to get past Putin's censorship)," posted a HackerNews user in reaction to the new 'event-source-polyfill'.
"To some, that's malware, whilst to some people in Russia, it could be valuable information, something helpful."
In the same thread, another reader states, while code changes interfering with the project's intended and expected purposes may be termed as "sabotage," the case of 'event-source-polyfill' doesn't really fit the definition:
"Sabotage, to me, explicitly means that the act was committed with the intent of derailing the project’s original purpose. This act seems orthogonal to the original intent of the project, so it’s underhanded but it's not really sabotage."
A debate further ensued on GitHub though, whether certain parts of the newly introduced code could break production apps in edge cases.
As a caution, some have pinned their 'event-source-polyfill' version to the earlier, safe version 1.0.25.
Alternatively, one can always clone (fork) trusted versions of an existing open source project and opt to maintain these versions themselves, as opposed to indiscriminately fetching the latest official releases.
Redefining open source
Open source software largely started out as a way to promote an "open development process," simplify licensing, and better engage with the users and a community of developers who can peer-review and improve software through active participation.
Open source registries like npm, PyPI, and RubyGems are therefore set up in a manner that minimizes barriers to entry. These registries let anyone publish software packages that are ready for consumption by novices and hard-core professionals alike.
While version control platforms like GitHub are traditionally associated with software development and source code, cost-free registries like npm simplify the hosting and distribution process for developers looking to ship and use each other's finished apps that run out of the box.
But, as with any system that's open to the public, software repositories can and often face abuse from malicious actors.
Traditional security incidents on npm centered around the distribution of typosquatted packages—such as an 'electorn' package published by a threat actor to trap developers installing Electron. Should the developer misspell 'electron' in their console, they'd end up with the attacker's malicious package.
In 2021, dependency confusion drastically gained momentum as an emerging attack vector against software supply chain attacks.
Major incidents also involved accounts of legitimate developers being hijacked by attackers who'd now publish new versions of real libraries laden with malicious code.
Both 2018's 'event-stream' and ESLint compromises, and this year's cases of 'ua-parser-js', 'coa', and 'rc' being hijacked to serve malware are examples of this problem.
But the recurring incidents of developers voluntarily withdrawing their code from the internet or sabotaging their own projects to accentuate a bigger idea have prompted software consumers to re-evaluate the open source model as it stands today, and engage in a public dialogue that is overdue.
While current protestware may be centered around the war, that doesn't mean it always will be limited to select trending issues.
Developers have discovered an avenue of creative self-expression that no longer restricts them to just delivering expected functionality—a developer can, on a whim, decide to change their mind and their code as they please. A neglected premise of open source is that they always could.
Update Apr 12th, 02:51 AM ET: Added other examples: 'styled-components' and 'es5-ext' npm packages turned protestware. h/t Tzachi (Zack) Zorn.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now